While decentralization is expanding its boundary, cyber-attacks and hacking have been intensifying. Hackers have performed so many horrific digital thefts after finding bugs in the early stage of blockchain projects.
Flash Loan attacks have become the most devastating sort of cyberattack among all of these. It’s also a difficult challenge for developers to protect their projects from flash loan attacks as it’s the cheapest and easiest to get away with.
Flash loan attacks are the opportunity where the hackers reap the benefits by creating an arbitrage opportunity and exploiting Dapps using the help of smart contracts. Flash loans provide a significant security risk. However, flash loans are here to stay, and we must consider the influence they will have on DeFi security in the future.
In this article, you will get a basic understanding of flash loan attacks and how hackers can use it for their benefit to steal millions worth of funds in no time. You’ll also find some crucial steps to prevent flash loan attacks.
So, let’s begin.
What are flash loans?
Flash loans are a type of uncollateralized loans executed by smart contracts. With a flash loan, a user can borrow as much as they want without any collateral to start with. The only condition for them is that they have to repay their loan in the same transaction. The Defi protocol Aave introduced the Flash Loan.
The main benefit of Flash loans is that you can use them to gain arbitrage advantages among two different decentralized exchanges such as Uniswap and Compound.
Let’s try to understand this with an example, assume you have two different crypto exchanges: Exchange A & Exchange B.
Exchange A shows a $100 price of some crypto, while Exchange B reflects a $110 price of the same crypto. Using flash loans you can take advantage of this price difference and can reap profits out of it.
There was a time when to use flash loans, one required in- depth knowledge about programming to create a smart contract. Luckily, now there is a platform like Furucombo, where you can take advantage of flash loans with zero knowledge of coding.
How do flash loan attacks work?
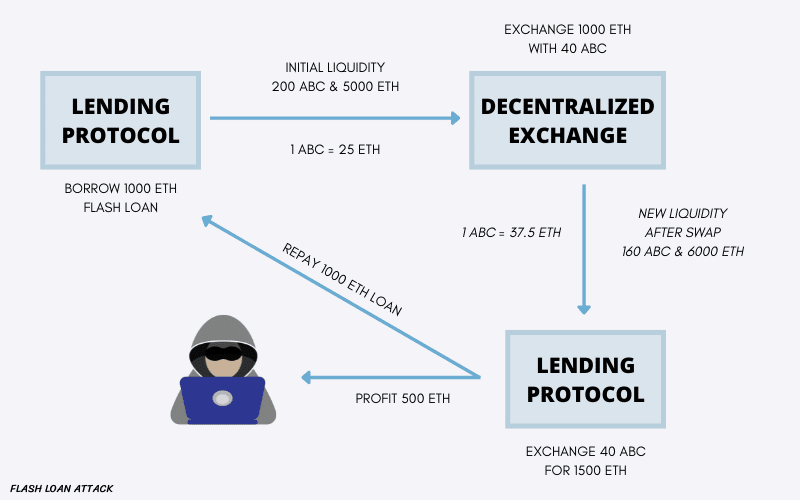
For example, if you want to borrow $70,000 in ETH, a lending protocol will provide it to you right away, but that doesn’t mean it’s yours. You must do something with the borrowed money in order to repay the debt and possibly pocket any remaining funds.
Initially, the attacker borrows certain assets in huge amounts from a protocol. Then the attacker utilizes it to manipulate a certain liquidity pool of the protocol, preferably with low liquidity. By doing this the hacker is able to take a big portion of the token and dump it on the market, causing the price to drop. The hacker then uses the same platform to repay the loan amount.
To make this work, the process must be quick, and the debt must be paid back in a single transaction. If an unpaid smart contract will reverse the transaction as it never happened. Attackers of flash loans thrive on devising new ways to distort the market while still adhering to the blockchain’s laws.
Why are these attacks so common in DeFi?
Flash loan attacks are a lethal combination of low-risk, low-cost, and high-reward tactics from the standpoint of a criminal. These attacks are increasing at a faster rate for two major reasons.
1. They are affordable
Flash loan attacks are quite economical as, here the hacker needs only 3 things: a computer, an internet connection and most importantly, ingenuity.
The only thing that matters here is the planning because it takes very little time, ranging from a few seconds to a few minutes at the very most.
2. They have a lower risk
Because no traces are left after an act is completed, no single attacker has been recognized to this day. This occurs as a result of the permissionless network and the many instruments that obstruct identity.

3. Hackers don’t require much capital
Because flash loans allow hackers to temporarily gain access to millions of tokens, they can carry out a digital theft with a pre-planned blueprint. After they’ve completed all of the settlements required to drain millions of dollars in tokens, blockchains just ask them to pay negligible gas fees, which are well worth it.
I mean who wouldn’t pay a small sum, if the golden goose awaits at the end !!
Why are flash loan attacks attractive to hackers?
To perform flash loan attacks, hackers don’t need much assets or capital to invest before the attack. All they need is just excellent programming skills to exploit the smart contracts.
Flash loan attacks are unique. There is no risk and no opportunity cost with flash loans! Because the borrower “froze time” for the duration of their flash loan, the system’s money was never at stake or constrained in the view of anybody else, and so could not have earned interest elsewhere.
There are so many instances when attackers have executed a flash loan attack after just paying negligible gas fees.
Furthermore, hackers can easily erase their footsteps once they have to transfer the funds into their crypto wallet addresses. Hackers can easily scatter their funds by using different protocols such as Tornado Cash or others.
Top of all this, the entire hacking process can be completed in a few seconds or minutes.
How to prevent flash loan attacks?
A dApp can protect itself from flash loan assaults in a variety of ways, the most prevalent of which are:
1. Using Decentralized Oracles
The use of decentralized oracles that use many sources to determine the “real price” is by far the safest choice.
Some decentralized oracles, such as Umbrella Network, go a step further and commit data to the Blockchain to assure its reliability.
2. Pricing Updates at a High Frequency
Here, there is an increase in the number of times the liquidity pool consults an oracle for a new price. The aim is with more changes, the price of a token will rise more quickly. This results in an invalid attempt at the price valuation.
3. Time Weighted Average Pricing (TWAP)
The TWAP suggests averaging prices over several blocks. Because the entire series of assaulting transactions must be done within the same block, flash loan attacks are reduced. Although, without exposing the entire blockchain, the TWAP cannot be modified.
4. Audit Protocol
Delay is sometimes preferable to a hurried protocol implementation. The evidence from previous protocol attacks suggests that they were not audited before being deployed. By having their protocol audited by outside parties, faults and weaknesses in the protocol can be fixed. Reputable companies such as Certik, Chainsulting, and OpenZeppelin conduct thorough audits in order to offer bug-free protocols.
Cases of flash loan attack
With the infamous 2017 DAO breach on Ethereum, we saw an illustration of the whole Flash loan attack. Since then, 51 percent of protocols have been targeted for financial benefit.
A few of the famous attacks are enlisted below:
- Bzx: The first found flash loan attack
In the history of DeFi, Bzx protocol was the first one to get attacked by a flash loan. The attacker acquired 10000 ETH using flash loan from a lending DApp dYdX. The amount was divided into two parts and used on Compound & bZx platforms.
To secure a loan of 112 wBTC, the attacker first transferred ETH to Compound protocol and collateralized it. In the meantime, 1200 ETH was delivered to bZx, which was used to short ETH in favor of wBTC.
Attackers used the Kyber Network to trick Uniswap, a dex with limited liquidity at the time, into sharing data with bZx in order to push the price of wBTC. After that, the attacker dumped the wBTC he had borrowed from the compound on Uniswap.
Now with (profits in hand/ 1193 ETH in their pocket) the attacker paid back the loan of dydx and left bZx with an uncollateralized loan.
The attacker was able to fool the system by engaging in numerous transactions with five different DeFi protocols. He deceived the bZx protocol into believing WBTC was worth much more than it was.
- Cream Finance
In August, Cream Finance, a decentralized finance (DeFi) lending platform, was hacked. Hacker exploited a weakness in the $AMP token contract to steal $18.8 million in a flash loan assault.
The protocol informed the community that the attack resulted in the loss of 418,311,571 AMP and 1,308.09 ETH.
Before borrowing 19 million AMP, the hacker took out a 500 ETH flash loan and placed the money up as collateral.
Before self-liquidating, they exploited the $AMP contract’s reentrancy problem to borrow an extra 355 ETH within the $AMP transaction.
The hacker carried out this operation across 17 transactions, resulting in the loss of nearly $18 million.
Endnotes
Flash loan attacks have become rampant, and they’re here to stay, at least for the time being. Despite all of the suggested solutions, it’s important to remember that DeFi technology is still nascent and developing.
Hackers discover new flaws every week before they’re patched. Developers can only cope with this situation by searching for solutions before they are attacked. So, as a smart user do your research and consider the risks involved before interacting with any protocol.







